What is it?
If you work in accounts or finance, you may have had a CEO fraud email (if not, I can say with confidence you probably will get one soon). They’re those emails that seem to be from your MD (or company director, or CEO) and they’ll say something like:
- “I urgently need to sort out a wire transfer. Let me know when you can sort it out for me and I’ll send the details”
- “I’m in a meeting and need to sort out a payment. Please send £10,000 to this account”
And so on and so on…
Your MD’s name will be in the “from” field and the domain may even be so similar to yours that you don’t notice it isn’t actually yours (for example, “john.smith@bgcompany.com” instead of “john.smith@bigcompany.com”), or it may actually be your domain (for reasons too technical to go into here).
And of course, it’s s scam, and a very successful and growing scam. The last figures I saw were that it had grown by over 300% in the past year and it’s netted scammers upwards of $2bn in the past three years.
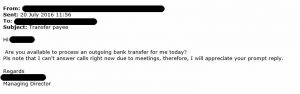
Here’s a real example (click to view, details removed to protect the innocent):
So how does CEO fraud work?
What the scammers do is:
- Find out from various sources who is the MD/CEO/Chairman of a company (Companies House, social media, Linkedin, etc. Anywhere, really)
- Find out who is the person responsible for finance from similar sources
- Do that for hundreds of companies
- Register a domain or throwaway email address
- If they don’t know the actual email addresses, assume that email addresses are in the form firstname.lastname@company.com (they nearly always are)
- Spoof an email from the first person to the second for all the companies they’ve researched (a script to do this is surprisingly easy to do)
- The first email says something like the first example above
- If you respond, they’ve got a sucker, and they’ll come back to you immediately asking you to transfer £20,000 or whatever to a bank account or via wire transfer
- Alternatively, they’ll just ask for the transfer straight out, like in the second example
- They get as much money as they can and disappear
It can’t usually be stopped by spam checkers because it’ll only happen over one day, so they don’t have time to react, and it’s an innocuous looking email with no attachments or links.
Another thing I’ve seen the scammers do in their fake emails is say “I’m in a meeting right now, but I need you to transfer £XXXX” (or “I’m on holiday right now, but I need you to transfer £XXXX”). One accountant – who didn’t fall for it, thankfully – asked me how they knew his MD was in a meeting. The answer is, they didn’t, but if you send 10,000 emails, all supposedly from company MDs, the chances are at least 1000 of them will be in a meeting, and that makes things much more convincing.
How do I stop it?
That’s surprisingly difficult. As I say, spam checkers are unlikely to work, and there’s no malware or viruses attached to the emails. You might have some luck with SPF records, but that’s only if they’re actually spoofing your domain. In the end, CEO fraud is simply social engineering , so educating staff is the only way to stop it. Make sure they know:
- Bad guys are out there, every hour of every day
- If the request is a surprise, it’s almost certainly fake
- Check and check again before doing anything. It’s better to be seen as a bit of a fusspot than somebody who cost your company 10s of thousands